Isolates and Containerized Processes
The evolution of computing paradigms has been a journey toward greater efficiency, scalability, and abstraction. From physical servers to virtual machines, and then to containers, each shift has aimed to optimize resource utilization and simplify deployment. Today, isolates are emerging as an innovative approach that builds upon and refines the containerization model.
Isolates are lightweight execution contexts that provide a secure, isolated environment for code execution within a shared runtime. Developed as part of the Chrome’s V8 JavaScript engine, isolates offer a sandboxed space where functions can run independently, without interference from other processes. This makes them particularly well-suited for serverless architectures and edge computing.
In this post, I’ll explore the architectures, performance characteristics, security models, and real-world applications of both isolates and containerized processes. By examining these aspects in detail, we can better understand their respective strengths and use cases in modern computing environments.
Containerized Processes
Containers are technologies that allow the packaging and isolation of applications with their entire runtime environment. By encapsulating an application and its dependencies, containers ensure consistent performance across different environments. In essence, they are a form of operating system-level virtualization, allowing multiple applications to run in isolated spaces while sharing the same OS kernel.
A virtual machine is a piece of software that emulates a complete computer system, running its own operating system and kernel in isolation from its host machine. While virtual machines offer another way to host multiple environments on a single server, they consume significantly more resources than containers.
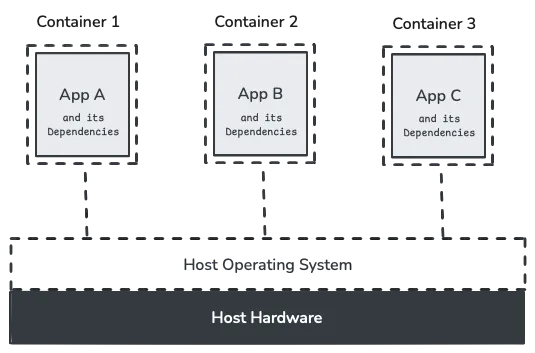
Containers offer several key advantages, including portability across any system supporting the container runtime, resource isolation between applications, easy horizontal scalability for handling increased loads, and consistent environments that eliminate deployment inconsistencies. However, they also face notable limitations. These include resource overhead from maintaining separate libraries and dependencies, significant startup times ranging from seconds to minutes that can impact performance-critical applications, operational complexity requiring orchestration tools like Kubernetes, and security risks where kernel-level vulnerabilities can affect all containers sharing the host OS.
Introducing Isolates
These limitations have led to alternative approaches, particularly isolates as implemented in Chrome’s V8 engine — Google’s JavaScript engine (named like the eight-cylinder engine) that can execute code both within and outside of browsers. This flexibility, combined with V8’s isolate architecture, provides enhanced resource efficiency, faster startup times, more granular isolation for better security, and improved scalability, making it a compelling alternative to traditional containerization.
V8’s runtime can manage thousands of isolates, switching between them seamlessly while maintaining complete memory isolation between each piece of code. This isolation ensures protection from untrusted or user-written code within the same runtime. Unlike virtual machines that require a complete environment setup, isolates are created within an existing environment, enabling extremely fast startup times and eliminating the cold starts typically associated with virtual machines.
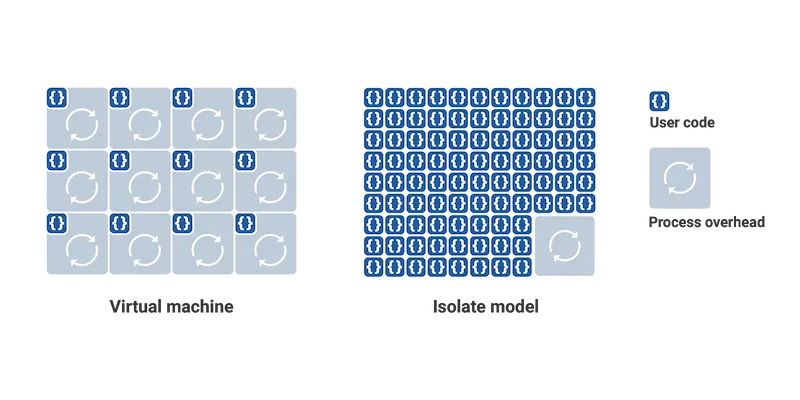
The figure above contrasts two approaches to running code: containerized processes and V8 isolates. In containerized processes, each instance requires its own language runtime, creating significant overhead. V8 isolates take a different approach — the V8 engine pays the runtime overhead only once at startup, after which it can execute hundreds of thousands of isolated scripts with minimal individual overhead. This architecture enables isolates to start approximately a hundred times faster than containerized Node.js processes, while consuming an order of magnitude less memory at startup.
V8’s Fine-Grained Sandboxing
A sandbox provides an isolated execution environment where software runs independently from other processes on the same machine. This isolation is a fundamental feature of Chrome’s V8 engine, enabling secure and efficient code execution through a sophisticated sandboxing architecture.
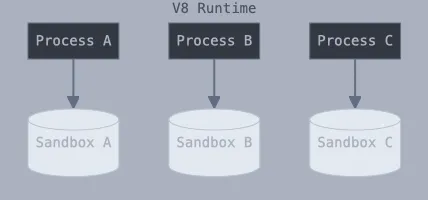
V8’s approach to sandboxing stands out from traditional solutions:
- Unlike enterprise sandboxing products that rely on isolated virtual machines, V8’s implementation maintains high performance.
- Each process operates in its own sandbox, ensuring complete separation of JavaScript functions.
- Memory isolation prevents code execution in one sandbox from affecting others.
While V8 provides the foundation for various JavaScript runtimes, it’s important to understand how other environments build upon it. Node.js, for example, is built on the V8 engine as a runtime environment for JavaScript, offering asynchronous execution capabilities and sharing V8’s open-source nature. However, it notably lacks V8’s built-in sandboxing features, distinguishing it from its underlying engine.
A runtime environment is the software infrastructure where code executes. While Node.js uses the ‘.js’ extension to denote its JavaScript association, this is purely nomenclature and doesn’t indicate a JavaScript file.
Compute Per Request Paradigm
Compute Per Request is a natural paradigm that aligns perfectly with the lightweight, ephemeral nature of isolates. This model proves especially valuable in serverless and edge computing environments, where minimizing latency and optimizing resource usage are critical.
Unlike typical containerized processes that require separate runtime environments, isolates provide lightweight, sandboxed execution contexts within a shared runtime. This architecture enables platforms to process requests with significantly reduced overhead, faster startup times, and more efficient resource utilization.
The alignment between isolates and Compute Per Request has led to its adoption by modern edge computing platforms like Cloudflare Workers, Deno Deploy, and Fastly Compute@Edge. These platforms demonstrate how the combination of isolates’ ultra-fast startup times and fine-grained resource allocation enables true request-level computation, delivering consistent performance at scale without the overhead of traditional containerization.
Limitations and Optimal Use Cases of Isolates
While isolates offer compelling advantages in startup speed, resource efficiency, and security through fine-grained sandboxing, understanding their limitations is crucial for making informed architectural decisions.
Language Support and Runtime Environment
Unlike containers that can package applications in any programming language, isolates are specifically designed for JavaScript and WebAssembly execution within the V8 engine. This specialization means applications must either be written in these languages or transpiled to them. Additionally, the V8 runtime environment may not provide all system-level functionalities available in a complete operating system environment, potentially limiting applications requiring low-level system access or complex dependency management.
Ecosystem and Standardization
The container ecosystem benefits from mature tooling and standardization through the Open Container Initiative (OCI), enabling portable deployments across different runtimes and cloud providers. In contrast, isolates are tied to specific runtimes like V8, and their ecosystem, while growing, hasn’t reached the same level of maturity in terms of orchestration, monitoring, and deployment tools.
Optimal Use Cases
Despite these constraints, isolates excel in specific scenarios that leverage their strengths. They are particularly well-suited for:
- Edge Computing: Applications requiring minimal latency and efficient resource utilization at the network edge.
- Serverless Functions: FaaS platforms handling high volumes of short-lived requests.
- Multi-Tenant Environments: Services executing user-provided code securely at scale.
- Per-Request Computation: Workloads requiring computation on a per-request basis without maintaining long-lived processes.
Conclusion
While containers remain valuable for many use cases due to their portability and consistent environments, isolates offer a compelling alternative for scenarios requiring rapid startup times and efficient resource utilization. They enable code execution at the network edge, which not only improves performance but also simplifies deployment and reduces costs compared to running code in a centralized data center.
As computing continues to evolve, especially in serverless and edge computing contexts, understanding and leveraging the strengths of both approaches will be crucial for optimizing application performance and resource usage. Selecting the right execution model depends on the specific needs of the application, and a hybrid approach may often provide the best balance between flexibility and efficiency.
References: Chrome’s V8; Cloudflare Workers; What is Chrome’s V8